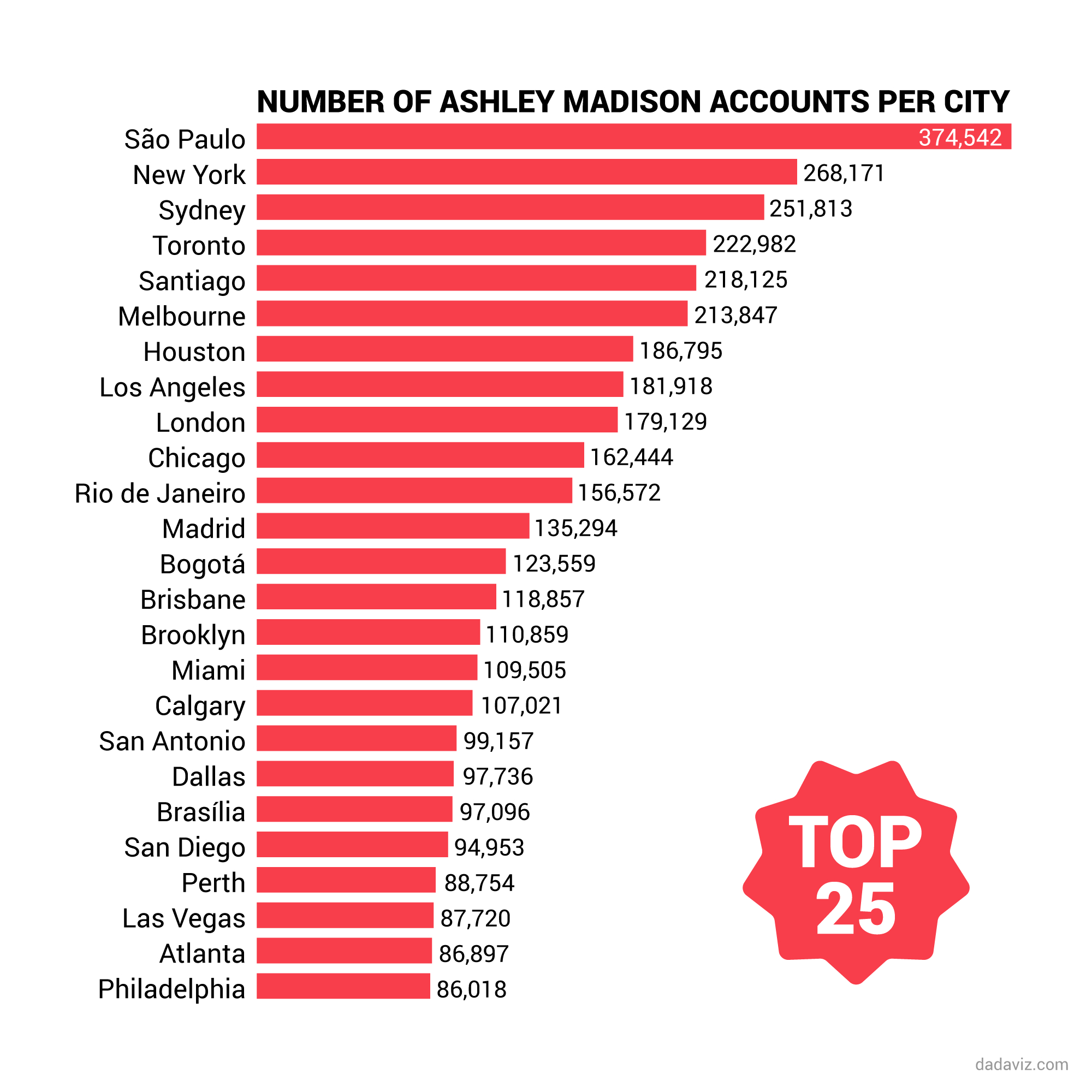
The Ashley Madison email list PDF has become one of the most controversial topics on the internet, sparking debates about privacy, ethics, and cybersecurity. The infamous data breach in 2015 exposed millions of users' personal information, creating a global uproar. This breach not only affected individuals but also highlighted the vulnerabilities in digital security systems.
With the increasing reliance on digital platforms for personal and professional activities, the Ashley Madison incident serves as a stark reminder of the importance of safeguarding sensitive information. Understanding the implications of such breaches is crucial for individuals and organizations alike.
This article delves into the details of the Ashley Madison email list PDF, exploring its origins, consequences, and lessons learned. By examining this case, we aim to provide valuable insights into data protection and cybersecurity practices.
Read also:Unlock The Secrets Of The Whispering Method A Comprehensive Guide
Table of Contents
- Biography of Ashley Madison
- Understanding the Ashley Madison Data Breach
- What is the Ashley Madison Email List PDF?
- Impact of the Data Breach
- Lessons in Cybersecurity
- Importance of Data Privacy
- Legal Implications
- Preventing Future Breaches
- Steps for Recovery
- Conclusion
Biography of Ashley Madison
Background of the Platform
Ashley Madison was launched in 2001 by Avid Life Media, a company specializing in online dating platforms. The website targeted married individuals seeking discreet extramarital affairs, positioning itself as a platform for "affair dating." Despite its controversial premise, the site gained significant popularity, attracting millions of users worldwide.
Data Table
| Founder | Noel Biderman |
|---|---|
| Launch Year | 2001 |
| Headquarters | Toronto, Canada |
| Users (as of 2015) | 37 million+ |
Controversial Nature
The platform's existence itself was a subject of debate, with critics questioning its moral and ethical implications. However, the 2015 data breach brought the site under intense scrutiny, as personal information of millions of users was exposed, leading to widespread backlash.
Understanding the Ashley Madison Data Breach
The Ashley Madison data breach occurred in July 2015 when a hacker group called "The Impact Team" infiltrated the site's database. The hackers accessed sensitive user data, including names, email addresses, credit card information, and other personal details.
Who Were the Hackers?
The Impact Team claimed responsibility for the breach, stating that they were motivated by the site's unethical practices. They demanded that Ashley Madison and its sister site, Established Men, shut down permanently. When their demands were not met, they released the stolen data to the public.
Read also:Puffer Jacket Outfit Ideas Stay Warm And Stylish This Winter
What is the Ashley Madison Email List PDF?
The Ashley Madison email list PDF refers to the compilation of email addresses extracted from the leaked database. This document contains millions of email addresses belonging to users who registered on the platform. The release of this list sparked panic among affected individuals, as their private information became publicly accessible.
How Was the Email List Compiled?
The hackers meticulously gathered user data from the Ashley Madison database and organized it into a downloadable PDF format. This list quickly spread across the internet, making it accessible to anyone with internet access.
Impact of the Data Breach
Personal Consequences
For many users, the breach had devastating personal consequences. Marriages ended, reputations were ruined, and some individuals even faced legal action. The exposure of their private information led to emotional distress and, in some cases, severe mental health issues.
Financial Implications
Financially, the breach resulted in significant losses for both users and the company. Users faced potential identity theft and fraud, while Ashley Madison incurred substantial legal and operational costs. The company also faced numerous lawsuits, further exacerbating its financial woes.
Lessons in Cybersecurity
The Ashley Madison breach highlighted critical vulnerabilities in cybersecurity practices. Organizations must prioritize data protection to prevent such incidents in the future.
Best Practices for Data Security
- Implement robust encryption protocols to safeguard sensitive information.
- Regularly update security systems to address emerging threats.
- Conduct employee training on cybersecurity awareness.
- Adopt multi-factor authentication for enhanced security.
Importance of Data Privacy
Data privacy is a fundamental right that must be protected at all costs. The Ashley Madison incident underscored the importance of safeguarding personal information in an increasingly digital world.
Protecting Your Privacy
Individuals can take proactive steps to protect their privacy online:
- Use strong, unique passwords for all accounts.
- Limit the amount of personal information shared on social media platforms.
- Regularly monitor financial accounts for suspicious activity.
- Enable privacy settings on all digital devices and applications.
Legal Implications
The Ashley Madison breach had significant legal ramifications. The company faced numerous lawsuits from affected users, alleging negligence and breach of privacy. Regulatory bodies also investigated the incident, resulting in fines and penalties.
Regulatory Response
Governments worldwide have since strengthened data protection laws to prevent similar breaches. The European Union's General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) are examples of such legislative measures.
Preventing Future Breaches
To prevent future breaches, organizations must adopt a proactive approach to cybersecurity. This includes investing in advanced security technologies and fostering a culture of security awareness within the workforce.
Technological Solutions
Emerging technologies such as artificial intelligence and machine learning can enhance cybersecurity measures by detecting and mitigating threats in real-time. Organizations should explore these solutions to fortify their digital defenses.
Steps for Recovery
For individuals affected by the Ashley Madison breach, recovery involves taking immediate steps to secure their personal information. This includes changing passwords, monitoring credit reports, and seeking legal advice if necessary.
Rebuilding Trust
Rebuilding trust after a data breach requires transparency and accountability from organizations. Companies must communicate openly with affected individuals and implement measures to prevent future incidents.
Conclusion
The Ashley Madison email list PDF remains a potent reminder of the vulnerabilities inherent in digital systems. The 2015 data breach had far-reaching consequences, affecting millions of individuals and prompting significant changes in data protection practices.
As we continue to navigate the digital age, it is imperative that we prioritize cybersecurity and data privacy. By learning from past incidents and adopting best practices, we can create a safer online environment for everyone.
We encourage readers to share this article and engage in discussions about data protection. Your feedback and insights can help raise awareness and drive positive change. Together, we can build a more secure digital future.
References:
- United States Federal Trade Commission. (2017). Ashley Madison Data Breach Settlement.
- European Commission. (2018). General Data Protection Regulation (GDPR).
- California Attorney General. (2020). California Consumer Privacy Act (CCPA).